The IoT market is exploding, and networks of connected devices aren’t coming to a store, home, or workplace near you. They’re already there, in increasing numbers. IoT implementations are driving huge gains in productivity and value across multiple industries. They’re behind improvements in customer satisfaction, patient care, and even fuel efficiency.
But the IoT is also at risk of outgrowing conventional cybersecurity methods and techniques. As it does so, it lays all those gains at risk, and leaves organizations open to familiar and unknown attacks.
In this post, we’ll use statistics to paint a picture of where IoT security is, and where it’s going, as well as a brief discussion of best practices to keep your organization safe.
Size of the IoT market
The IoT market is both large and growing. The rate of growth is accelerating too. Even a global chip shortage hasn’t slowed it significantly.
Intel says there are about 26 smart devices for every human being on earth. (Source)
The IoT is forecast to grow at a Compound Annual Growth Rate (CAGR) of anywhere between 10.53% (Source) and 31.2% (Source).
There were 12.3 billion active endpoints by the end of 2021, expected to rise to 27 billion by 2025. (Source)
Forecasts of IoT growth sometimes take account of the growth of 5G and the introduction of IPv6.
Currently, we’re using IPv4, which allows for 4.3 billion unique 32-bit IP addresses (they look like this: 132.24.338.2).
That’s too restrictive for our multi-device consumer expectations, let alone for 26 devices per person. (In fact, we blew through these by 2015. Network Address Translation (NAT) has been providing prosthetic additional IP addresses since then.)
Fortunately, IPv6 allows for IP addresses made up of eight hexadecimal groups of four digits to offer 128-bit IP addresses. There should be room for 3.4 x 1038 unique IP addresses with IPv6.
The result will be the loosening of a brake on IoT device numbers.
At the same time, IoT devices will be able to communicate much faster thanks to 5G, which will allow for connections up to 20 gigabits per second. (Source)
Factor in faster communication and vastly higher numbers of connected devices, which will allow industrial use cases to mature and spread, and Juniper Research’s prediction of 83 billion IoT devices by 2024 makes sense. (Source)
Which industries are adopting IoT?
Almost all major industries are adopting some element of IoT. However, manufacturing, logistics, healthcare and retail are leading the way.
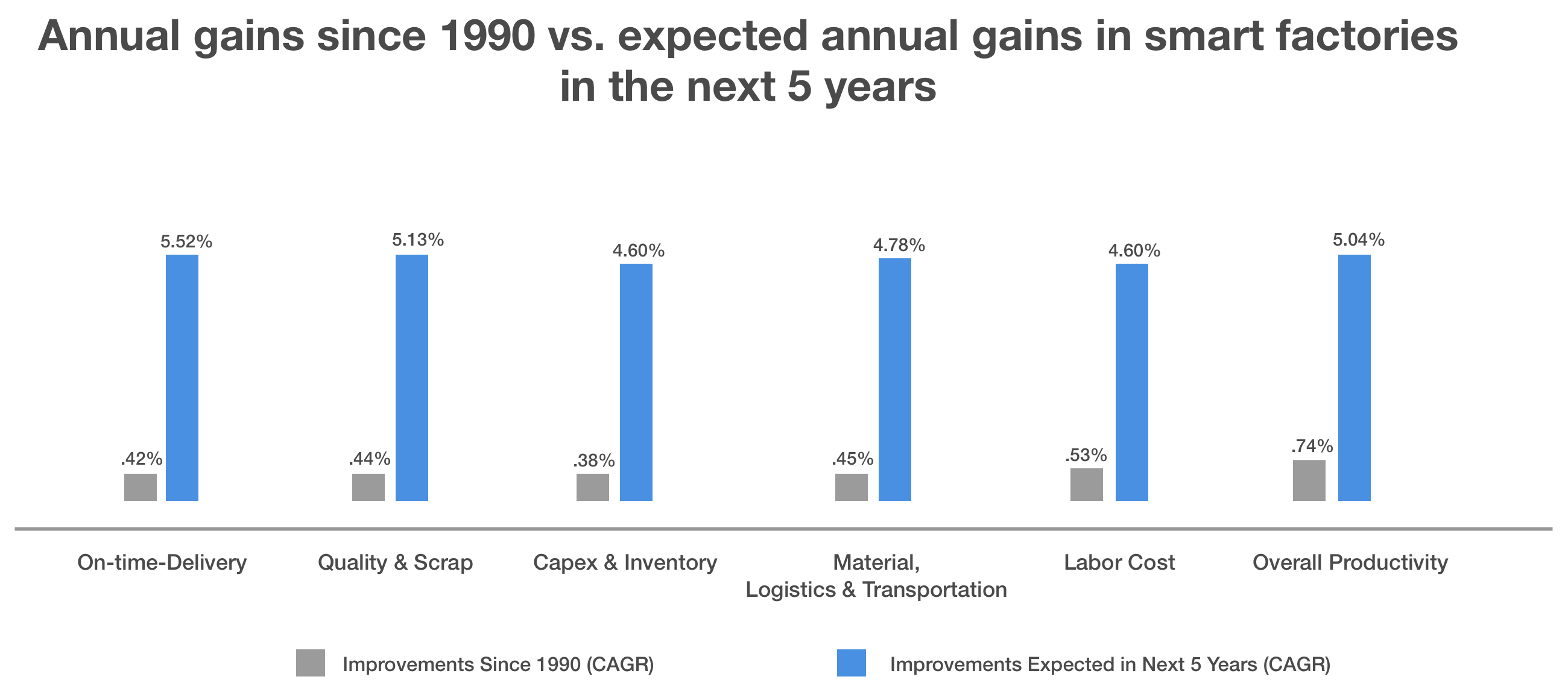
Manufacturing is one of the earliest-adopting sectors for IoT. Smart factories in North America alone are expected to be worth more than $500 billion by 2022. (Source)
Smart factories could 7X productivity by 2022. (Source)
76% of manufacturers have plans for a smart factory initiative or have already launched one, but just 14% are satisfied with the results so far. (Source)
Increases like these will revolutionize manufacturing, which has been a low-margin industry with slow growth in key areas for decades.
Manufacturing isn’t the only industry affected by the IoT revolution.
94% of retailers thought the benefits of implementing IoT outweighed the risk. (Source)
More than half of US hospitals have a remote outpatient monitoring system. (Source)
Healthcare IoT is expected to grow with a CAGR of 18%. (Source)
The global market in IoT healthcare was $60 billion in 2019, expected to rise to 260 billion by 2027. (Source)
The global market for IoT in logistics and transportation is forecast to grow at a CAGR of 12.4%. (Source)
54% of transportation and logistics companies plan to use IoT to monitor environmental changes. (Source)
The state of IoT security
IoT security is a multifaceted problem. IoT networks face unprecedented challenges, thanks to a large attack surface and easy lateral infections. Too few organizations follow best practices, too many are unprepared for the threat environment, and the number and sophistication of potential attackers is growing.
From January to June 2021, there were 1.5 billion IoT security breaches. (Source)
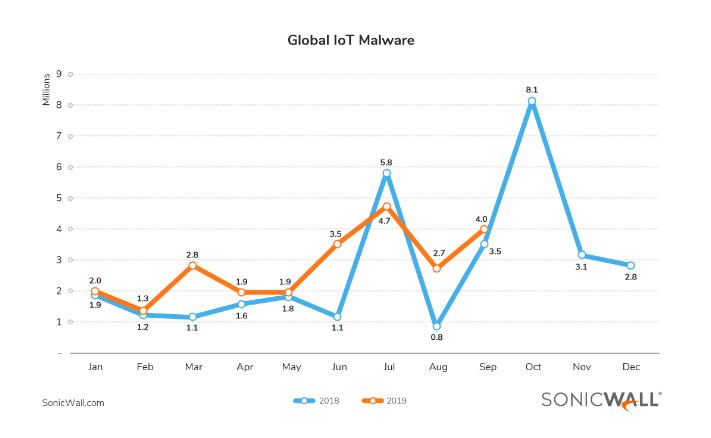
Global IoT attacks rose 33% year-on-year 2018-2019. (Source)
In a ‘honeypot’ study, which uses software to imitate vulnerable IoT devices so it can collect data on attackers, Kaspersky found 58% of attackers used telnet. The top three goals for attackers were cryptocurrency mining, DDoS attacks, and theft of confidential data. (Source)
The IoT security market is forecast to be worth $18.6 billion in 2022, up from $15.8 billion in 2021. (Source)
The biggest attack vector is device vulnerabilities:
The biggest risks for enterprises are cameras and printers:
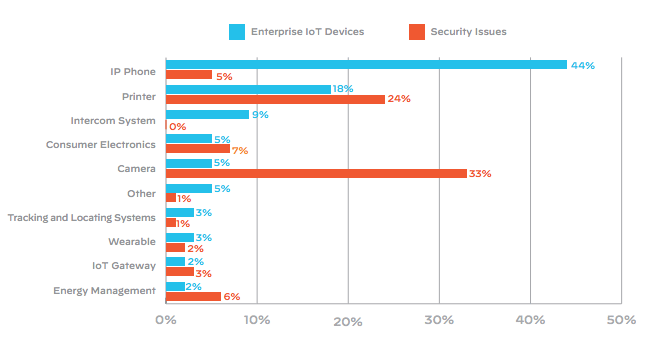
Cameras and printers are vulnerable because they’re easy to buy, install and operate. They’re often consumer-grade devices, but any connected device is an entry point to a company’s network.
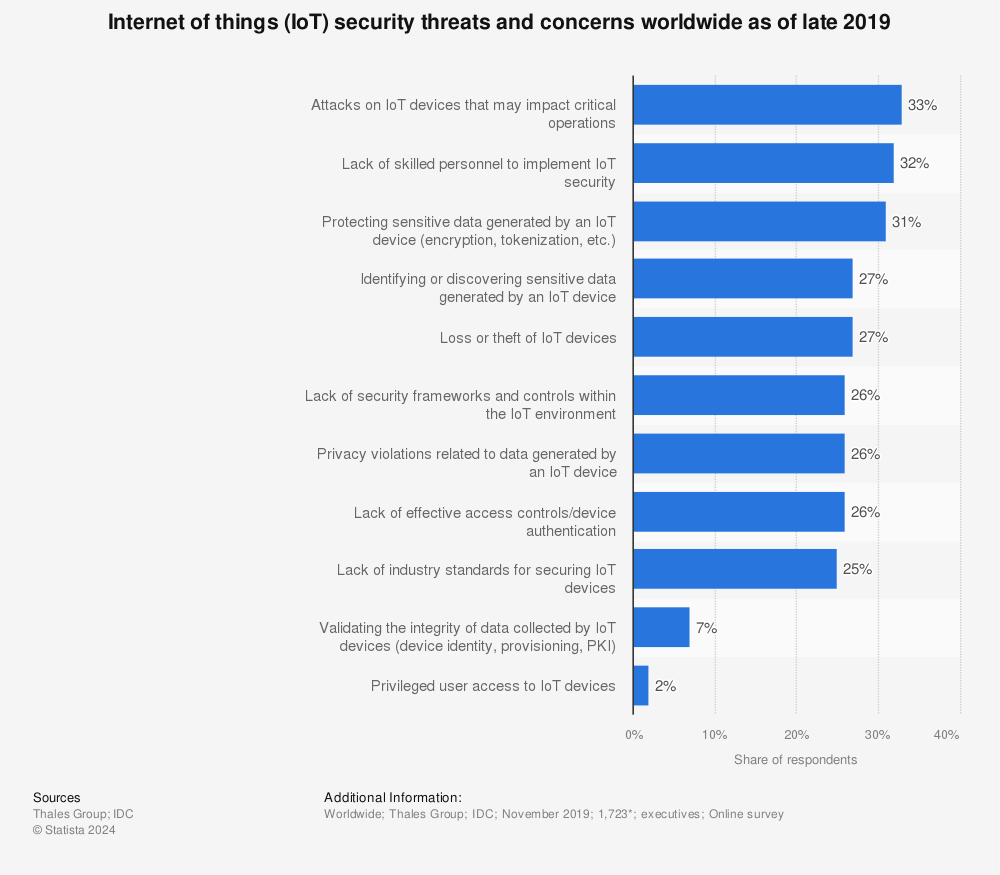
The top concern voiced by companies was deliberate attacks that could affect operations, with 33% saying it was their main issue. (Source)
The proportion of enterprises that rated IoT security a priority rose from 53% in 2028, to 57% in 2020. (Source)
Enterprises tend to address IoT security through the lens of cloud security they’re already familiar with. More than 70% of those enterprises that picked Security as a key purchasing factor rated device-to-cloud security as ‘very important.’ (Source)
Deliberate attacks
How are hackers attacking devices and networks?
Fewer than 42% of organizations can identify an insecure IoT device. (Source)
Average time for an IoT device to be attacked once it’s connected to the internet: less than 5 minutes. (Source)
Costs to rent a botnet based on IoT devices start at 35¢. (Source)
Cost to acquire an individual’s ‘fullz’ — personal data packages that can be used to steal their identity: starts at $4. (Source)
How much IoT traffic is unencrypted? 98%. (Source)
57% of IoT devices are vulnerable to medium- or high-severity attacks. (Source)
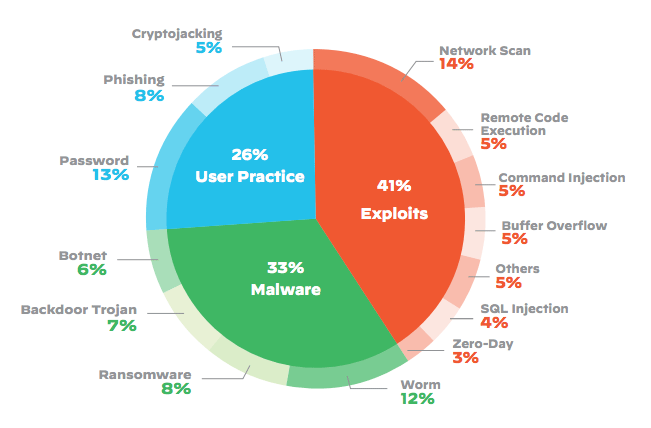
41% of attacks exploit device vulnerabilities. IT-borne attacks scan through network-connected devices in an attempt to exploit known weaknesses. (Source)
Healthcare is particularly vulnerable.
72% of healthcare VLANs mix IoT and IT assets, allowing malware to spread from users’ computers to vulnerable IoT devices on the same network. Just 3% practice good network segmentation. (Source)
83% of medical imaging devices run on unsupported operating systems, a 56% jump from 2018. When Windows 7 reached the end of its supported life, medical devices went right on using it, radically increasing their vulnerability. Now, 51% of threats against healthcare organizations involve imaging devices. (Source)
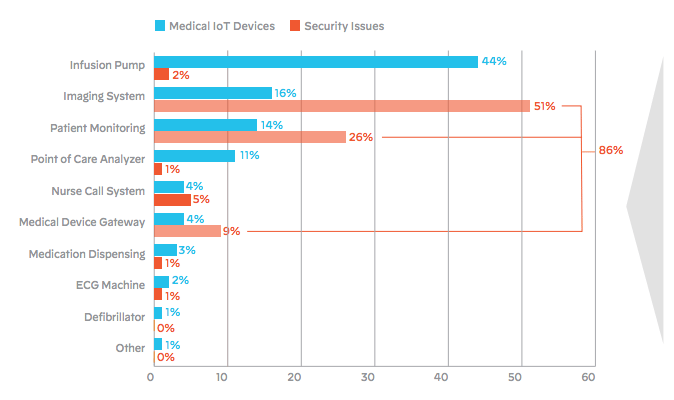
Medical devices are vulnerable because they have long lifespans and complex patterns of ownership in large institutions. They’re not maintained by their OS or device vendors. Their hospital IT departments don’t manage them, and the technicians who use them aren’t trained or employed to manage their security either. In consequence, they outlive all security provisions.
Targets
The main types of attacks on IoT devices don’t target operations directly. Instead, they seek to combine the two main values of the IoT to hackers: unprecedentedly large numbers of devices mean vastly larger attack surface and vast potential for botnet, DDoS and low-power, high-volume computing.
The number of DDoS attacks on IoT infrastructure increases 26% year-on-year. (Source)
Large-scale attacks grew fastest: attacks in the 100-200Gbps range rose 169%, those in the 200-300 Gbps rose 1,500%, and those on 300-400Gbps rose 3,600%. (Source)
Attacks on universities and educational institutions rose by over 500% in the second half of 2018 alone, while maximum attack size on airlines and specialized design services rose by 15,000% and 1,000% respectively. The number of attacks on passenger air transport rose 4,300%. This shows attackers diversifying methods and targets, preferring larger attacks. (Source)
The average increase in attack numbers in 2020 was 5%, indicating that cybercriminals took advantage of early IoT adoption vulnerability to establish a ‘new normal’ of high attack numbers and large size. (Source)
IoT security: the view ahead
68% of enterprises rate security integration with their existing practices as important. (Source)
85% of enterprises have changed their security practices as they adopted IoT; of those, 61% have switched to a security-first approach as a competitive advantage. (Source)
59% of enterprises trust cloud vendors to meet their security requirements. (Source)
Security was the main factor to consider when choosing an IoT vendor or partner for 57% of respondents in a 2018 survey. (Source)
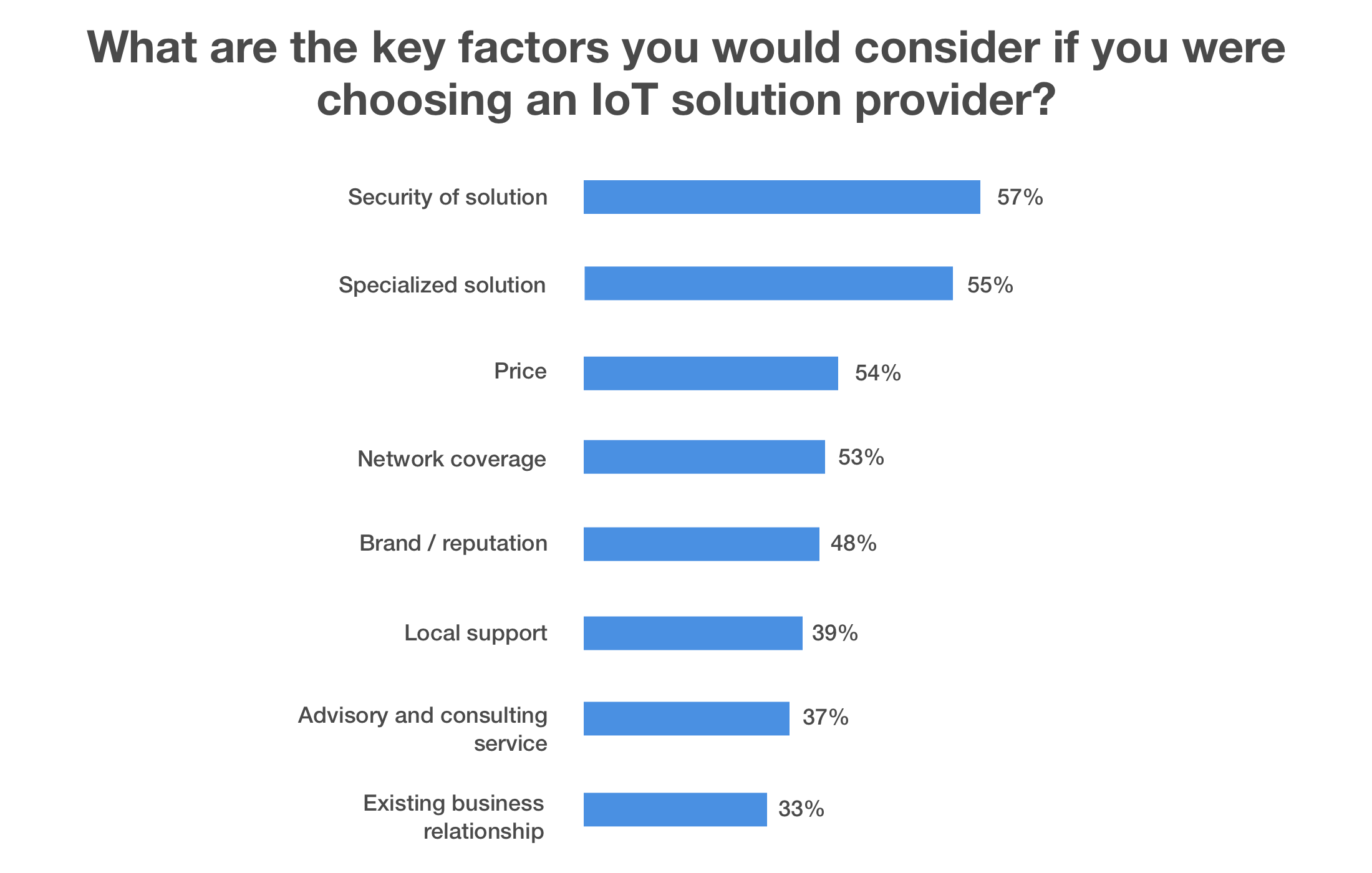
Takeaways: how organizations can improve their IoT security
Organizations can act to reduce their risk exposure by:
- Knowing your risks: know your network. Discover IoT devices on your network. (There are often many more than you expect.).
- Patch everything that’s easy to patch. This often plugs or sharply narrows major entry points like cameras and printers.
- Segment IoT and IT assets, and segment IoT assets across VLANs.
- Enable and use active monitoring.
- Think holistically across the network and across time. Plan for late-life and end-of-life when installing new devices, and consider the whole network when installing even very simple devices.
- Use product integrations to extend IoT security to every device.